CrowdStrike Addresses Recent Falcon Content Update Issue
CrowdStrike’s Falcon Update Causes Global System Crashes 🖥️🔵 On July 19, 2024, a routine update to CrowdStrike’s Falcon platform led to widespread system crashes and blue screens (BSOD) on Windows machines worldwide. The issue originated from a logic error in Channel File 291, affecting systems running Falcon sensors version 7.11 and above. CrowdStrike swiftly identified and rectified the problem by 05:27 UTC the same day, confirming it was not the result of a cyberattack. Detailed remediation steps were provided to affected users, while Linux and macOS systems remained unaffected.  
CYBERSECURITYCYBERCRIMECYBER UPDATES
Shivam Dharpure
7/21/20241 min read
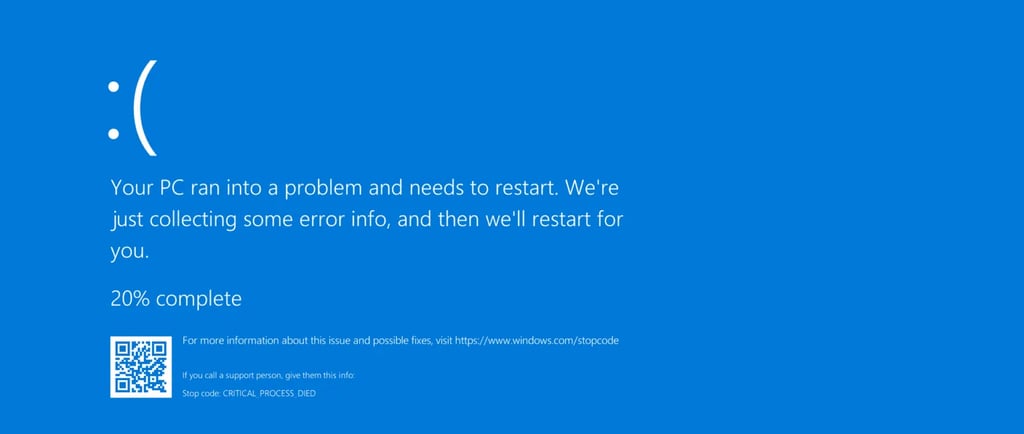
Recently, CrowdStrike encountered a technical issue with their Falcon platform. On July 19, 2024, at 04:09 UTC, a routine sensor configuration update for Windows systems led to unexpected system crashes and blue screens (BSOD). CrowdStrike quickly identified and resolved the problem by 05:27 UTC the same day. This incident was not related to any cyberattack.
**Impact:**
The issue affected customers running Falcon sensors for Windows version 7.11 and above who were online between 04:09 UTC and 05:27 UTC. These systems, having downloaded the faulty configuration update, experienced crashes.
**Configuration Files:**
The problem originated from the “Channel Files,” crucial components of Falcon’s behavioural protection, updated daily to address new cyber threats. This process has been part of Falcon’s design since its inception.
**Technical Details:**
The affected file, Channel File 291, located in:
```
C:\Windows\System32\drivers\CrowdStrike\
```
Is responsible for evaluating named pipe execution on Windows systems. The update aimed to mitigate threats from malicious named pipes but caused a logic error leading to system crashes.
**Remediation:**
CrowdStrike promptly corrected the logic error in Channel File 291. Detailed remediation steps and updates are available on their blog and Support Portal. Systems not impacted by this issue continue to function normally. Linux and macOS systems were unaffected.
**Solution**
CrowdStrike has provided a specific remediation step:
1. Navigate to the %WINDIR%\System32\drivers\CrowdStrike directory.
2. Locate the file matching “C-+919691568071*.sys” and delete it.
3. Detach the volume from the new virtual server.
4. Reattach the fixed volume to the impacted virtual server.
- Shivam Dharpure
Founder & Director
Visionary Bose Pvt. Ltd.
